You want to know how to increase yourInfolinks revenue (if you infolinks publisher) on your website or Blog. The following tips are the results of my experiment with Infolinks. If you are Infolinks publisher maybe the following tips useful for you to increase your Infolinks revenue and get more money from infolinks. But no guarantee your revenue will increase after do this tip and trick on your Blog or on your website. Some of my friends said after do this tips the infolinks CTR and revenue increases
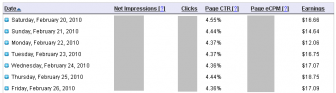
Here the screen-shot my Infolinks revenue before and after using this tips.
To use this tips and tips you must Login to your Infolinks account and then click “Integration Guide”. Here are tips you can do to increase your income with Infolinks
Tips 1: “Set links highlight color” and equated with the color the link in your blog.
Tips 2: Set underline link type to “dotted”, on my Infolinks account this tips increase CTR about 1%.
Tips 3: Set max allowed number of links per page to 6 or more. This tip will increase your CTR.
Tips 4: Set content category. On my experiment, business category gives more eCPM result.